Last Update: January 11, 2025
BY eric
eric
Keywords
In order to improve the security of email systems, organizations or enterprises implement DMARC policies to prevent email spamming and phishing attacks. Domain-based Message Authentication, Reporting, and Conformance (DMARC) is a critical email authentication protocol designed to protect domains from unauthorized use, such as spoofing.
However, such policies might also increase the difficulty for solving issues when an email fails to deliver, because now the troubleshooting has to involve IT professionals from two parties of both ends: the sender and the recipient.
Recently, emails sent by a client of mine to a government body were rejected. The error information provided by the email server was "451 4.7.5 Temporary error evaluating DMARC policy". This is not a common error, and there isn't much information available online.
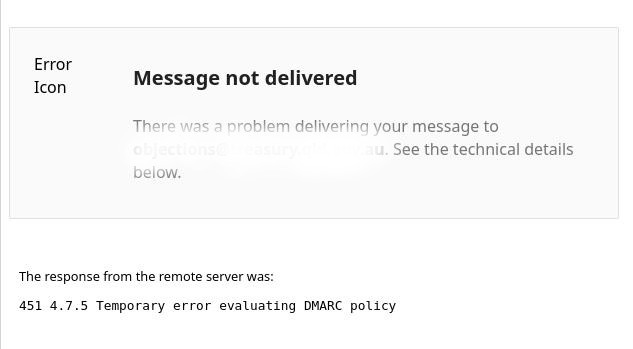
After a bit of research, some sources suggested it could be due to a DNS issue, where the DMARC record couldn't be found, at least temporarily. However, many attempts to resend the emails failed with the same error. This ruled out a DNS record issue because: 1) The record (hosted on Cloudflare) was double-checked and verified manually (_dmarc.______.com.au. 300 IN TXT "v=DMARC1; p=none; aspf=r"); 2) Emails to all other addresses, where DMARC policies were enforced, were successful; and 3) While a name server might experience temporary difficulties, it would rarely persist for an extended period. If that was the case, it would be a disaster for everyone, and my client's problem wouldn't be a lone case.
To get to the bottom of this, I had to contact the government agency's IT department, who provided helpful details about the situation. They explained that when an email reaches their server (mail gateway), their security products evaluated the email and flagged it as a threat due to the embedded links to my client's website (included in the email signature). My client's website was considered to contain malicious code, posing a potential threat. So the email security system stopped the message authentication process before it could finish the DMARC check. As the DMARC check could not be completed, the email was rejected. But because the check had started but was not able to reach the end, the error message was "451 4.7.5 Temporary error evaluating DMARC policy".
The website in question runs on WordPress with many popular plugins installed and activated. A quick check revealed some JavaScript code flagged as malware by a security checking website. However, throughout my own investigation with the help of ChatGPT (https://www.chatgpt.com/), no particular malicious code was found. Most javascript code in question was just part of a popular jQuery's plugin. The most invasive code was a tracking script used for Google Analytics. So what do we do now?
Possible Solutions
1. Remove Google Analytics Tracking Script
The first option is to remove the tracking script from the website. However, we will lose the analytics data and won't be able to improve the web traffic of the website. As for business, the understanding of user engagement is important to understand how users interact with the website, and we need to keep the analytics data to improve the website.
2. Whitelist Sender's Domain in Recipient's Server
The second option is to whitelist the sender's domain in the recipient's server. However, this can only be done by the recipient's system administrator and only if they really consider my client's email and website pose no threat.
3. Remove the Email Signature
This could be the most simple solution. As recommended by the system administrator from the government agency (Thanks Tim Sudholz for the suggestion), just removing the email signature before sending the email. As long as there is no link in the email, the email security system will not start a security check other than other standard checks, such as the DMARC check, spam check, etc.
Previous Article
Next Article

Jan 10, 2025




Comments (0)
Leave a Comment