Features
featured articles

BY eric
Feb 10, 2026
Router Down! My 3-Day Battle with Meraki, Ubiquiti & VLANs
A real-world network disaster story: router failure, emergency replacement, and the VLAN gotcha that almost broke everything

BY eric
Feb 10, 2026
RDP 'Please Wait' Black Screen? A Simple Fix
Fix RDP black screen with 'Please Wait' message by updating Windows - a simple solution that works.

BY eric
Jan 19, 2026
China & Japan at a Glance: Cashless Futures and Electric Cars
Technical insights on digital payments and EV adoption across China and Japan for tech travelers
BY eric
Dec 08, 2025
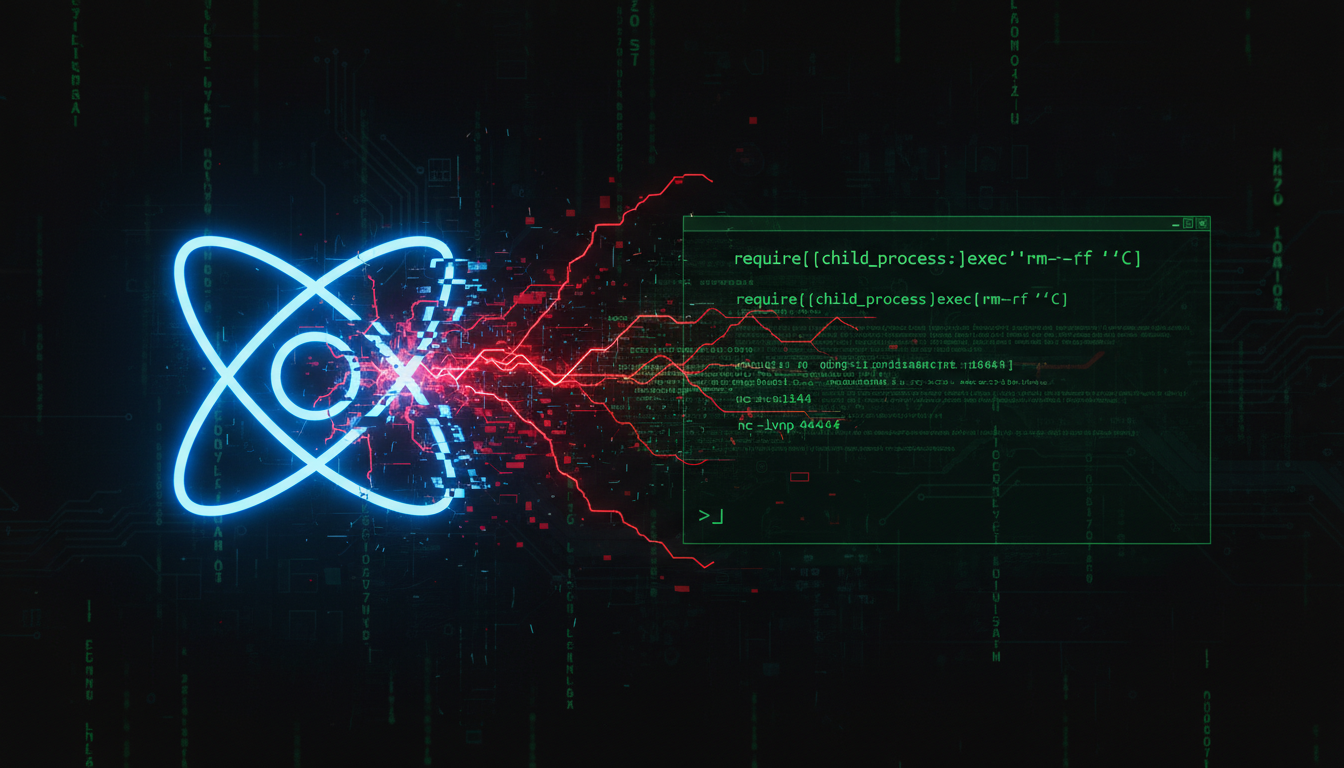
React2Shell: Critical RCE Flaw in Next.js & How to Fix It
Critical CVE-2025-66478 vulnerability allows remote code execution in Next.js applications worldwide.

BY eric
Dec 04, 2025
Escaping VirtualBox Hell: How I Migrated Windows 11 to KVM with AI
When VirtualBox kept freezing my Windows 11 VM, I turned to KVM/QEMU. The problem? Nobody remembers all those command-line incantations.

BY eric
Dec 03, 2025
AI Found the Simple Fix for My Shaking Mower
How AI helped diagnose a violent mower shake caused by a tiny wood chip, saving time and guesswork.

BY eric
Dec 03, 2025
AI Fixed My Shaky Washer: A Troubleshooting Guide
How AI helped diagnose and fix a vibrating washing machine through step-by-step troubleshooting.

BY eric
Dec 03, 2025
How to put your baby, sorry, your Linux box to sleep
A deep dive into troubleshooting Linux suspend issues, from USB controllers to sleep modes, and how AI transformed a potentially frustrating debugging session into a systematic investigation.

BY eric
Nov 03, 2025
AI Coder Showdown: Gemini vs. Claude vs. Codex
A developer's honest take on Google Gemini, Claude Code, and OpenAI Codex for programming tasks.

BY eric
Oct 30, 2025
From Hours to Seconds: AI-Powered Troubleshooting Thunderbird Browser Issue with Claude Code
How I used Claude Code to instantly fix a frustrating Thunderbird browser configuration issue that would have taken hours to troubleshoot manually.